Highlight of features:
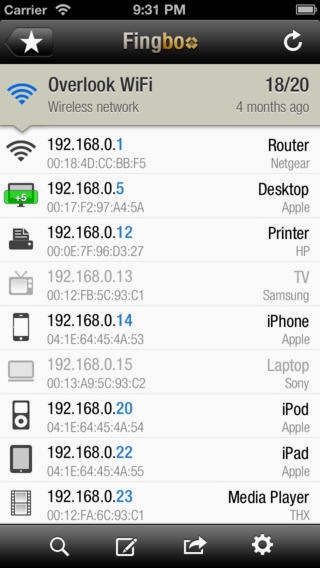
+ Discovers all devices connected to a Wi-Fi network. No limitation!
+ Displays the MAC Address and up-to-date Vendor names.
+ Customize names, icons and notes.
+ Wake On LAN. Switch on your cable-connected devices.
+ History of all discovered networks. You can review and edit your past scans at any time, also offline.
+ Checks the availability of Internet connection, reporting the geographic location of the ISP (Internet Service Provider).
+ Share a detailed report of any scan via email
+ Search devices by IP, MAC, Name, Vendor and Notes
+ In-app settings
+ Scans the open ports to find available services. It uses a fast engine that supports hundreds of well-known ports, that you can customize with your own
+ Translates IP addresses to its Domain Names, and reverse
+ Works also with hosts outside your local network
+ Tracks when a device has gone UP or DOWN, keeping disconnected devices in the list.
+ Discovers NetBIOS names.
+ Supports identification by IP address. Allows to customize nodes hidden behind a network switch.
+ Can sort devices by IP, MAC, Name, Vendor, State, Last Change.
+ Free of charge, Free of Ads
+ Integrates with Fingbox to sync and backup your customizations, merge networks with multiple access points, monitor remote networks via Fingbox Sentinels, get notifications of changes, and much more.
Fing is born from the ashes of the famous Look@LAN, with a brand-new engine that makes it even faster and smarter! Available also for Windows, Mac OS X, Linux and more platforms!







.png)




















